Check Point Software Links Pay2Key Ransomware to Iran
The Pay2Key attacks date back to last June.
Pay2key ransomware from Check PointLast week Check Point Software revealed the Pay2Key ransomware attack which had affected a number of Israeli companies. Now Check Point has revealed that it was able to track Pay2Key back to its source – Iran!
Ransomware works by taking control of a victim’s computer or even the entire systems of a private organization through a type of computer virus. Thea ttackers then extort a fee in exchange for returning control of the computers affected to their owners. The people behind Pay2Key have demanded payments of more than $100,000 in Bitcoin to regain control of their systems.
The Pay2Key attacks date back to last June. Check Point revealed that this ransomware hits victims at night, after midnight, when a company is not likely to have actively working IT teams.
The initial infection is presumably made through RDP connection. A program named “ConnectPC.exe” is then used to control all outgoing communication between all ransomware processes within the network and the attacker’s from this point on.
–
Several Israeli organizations reported over the past week they were attacked with a previously unknown #ransomware variant names #Pay2Key. The attacks are still under investigation, but we would like to offer our initial analysis and relevant #IOCs. https://t.co/q7DyJsyVHi #IR pic.twitter.com/Hp7abi9Jav
— Check Point Software (@CheckPointSW) November 11, 2020
Check Point explained last week in a blog post that, “To our surprise, the Server wasn’t an external command and control server, but rather the IP of the initial infected machine. Thus, we believe that the original machine was using ConnectPC.exe as a utility to relay communication from victims inside the organization to the external control server.”
“This approach increases the chance that the different machines will be able to communicate because internal communication is more likely to be allowed. It also decreases the chances that the address of the command and control will be revealed by analysts as there is only one machine in the organization that knows of it.”
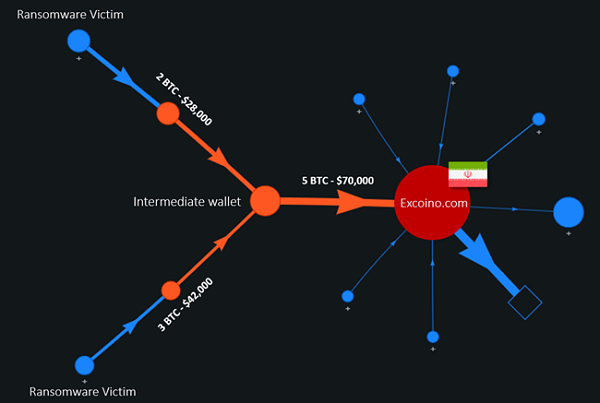
Now Check Point Software says that by simply following the money the company’s researchers were able to determine that Iran is the origin of the Pay2Key ransomware virus. It did so by watching the bitcoin “wallets” into which ransom paid by some of the victims went.
The same wallets were reused for the ransom payments of different victims. The bitcoins were then transferred to an intermediate wallet and the to a final wallet address associated with a high activity cluster. Check Point used WalletExplorer service to help uncover the location of the final wallet.
This led to Excoino which is an Iranian company that provides secure cryptocurrency transactions services for Iranian citizens.
Most ransomware attacks are just about the money. Hackers use them to steal. Nothing more. While it could be that the people behind Pay2Key are only looking for a payday, this is highly unlikely.
Iran has stepped up its cyber attacks on Israel recently. And it really stretches credulity to think that the Iranian government does not control any and all such activities coming from within their country.
Read more about: Check Point Software, Pay2Key